Carders have been operating since the 1980s, using a variety of methods to steal funds. As with any cybercrime activity, bad actors are constantly evolving their tools and techniques. With the proliferation of ecommerce and the ease of access to merchant accounts through payment facilitators, there are a growing number of vulnerabilities that can be exploited by carders.
While it’s great that an honest, budding entrepreneur with a website can gain easy access to electronic payment processing, the unfortunate flip side is that the bad guys can, too. Today, hundreds of payment facilitators offer services to merchants, allowing them to bypass the process of obtaining a merchant account directly through the bank. This streamlined offering is attractive to fraudsters as well.
Why is merchant-based carding gaining prominence?
A trend has emerged whereby carders set up fake stores and open merchant accounts with payfacs to cash out stolen credit card funds. While it is by no means a new scheme, changes in the ease of access to payment infrastructure have made it more popular.
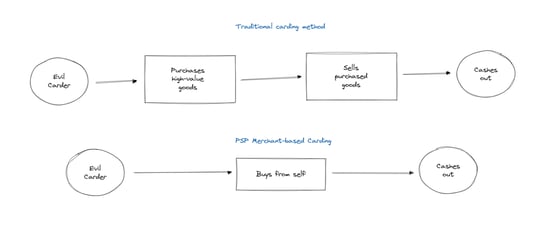
The main advantage for bad actors in this scheme is the ease of “cashing out.” In other carding schemes, stolen cards are used to buy high-value goods or stored value items such as gift cards. These are then resold to eventually monetize stolen card funds, allowing criminals to skip the middleman and pay themselves directly.
Various guides exist on both the dark and clear web as to how to conduct merchant-based carding. Many of these guides include instructions on how to bypass anti-fraud and KYC protocols, making the method attractive to fraudsters. Once a single “store” is successfully established, they will set up multiple fake stores in advance to continue to another when one account gets shut down.
How does merchant-based carding work?
- Our not-so-friendly carder acquires stolen credit card details – usually on the dark web or in hacker forums.
- Next, our carder is going to create a completely made-up website, with some completely fake products or merchandise.
- This website convinces a bank or payment facilitator to grant them access to the wonderful world of credit card acceptance.
- An external bank account, often opened with a fake or stolen identity, will be linked to this new merchant account.
- The fraudster uses the stolen credit cards to purchase their own products while employing tools to avoid fraud detection.
- They then transfer the earnings from these “sales” to an external bank account and gain access to the funds.
Efficiency is the goal for everyone – including criminal carders
Best practices for preventing abuse
When onboarding new merchants, organizations should consider the following best practices if they suspect a merchant may be malicious:
- Check for signs the website may not actually be intended for an outward facing audience (e.g., lack of checkout flow, non-sensible pricing, typos, poor user experience, mismatching contact detail, plagiarized content, etc.)
- Examine the transactions for suspicious patterns (e.g., round transaction amounts, odd purchasing hours, patterns in buyer details etc.)
- Make use of third-party tools such as MerchantView, which help to monitor merchant risk and suspicious activity to protect against fraudulent schemes such as carding.